|
Developers' Resources: LDAP Authentication
To help developers use LDAP as a method of authentication
and authorization, we have made available:
These documents provide guidelines for
configuring LDAP search and authentication requests. The more specific these
requests can be the better the performance will be for all applications using
the ldap service.
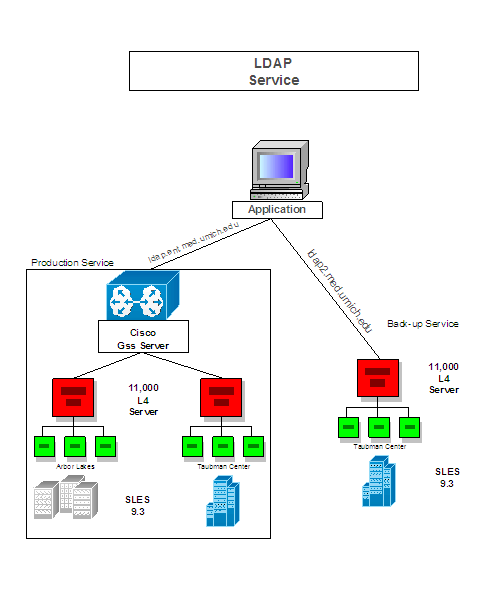
LDAP Service:
This diagram depicts the general layout of our
production LDAP infrastructure. The IDM team provides the production service,
a back-up production service, and a pre-production service (not shown).
For connection specific settings see the following LDAP resource topics.
LDAP Authentication
Best Practice—How to Authenticate to LDAP:
This provides guidelines for configuring LDAP search and authentication
requests. The more specific these requests can be the better the performance
will be for all applications using the ldap service.
When making LDAP calls, the following guidelines should be used whenever
possible:
1.) Define Search Base:
The search base is the point in the ldap tree where a search begins. Leaving
the search base undefined, or searching from RootDSE causes the ldap search
engine to traverse the entire data store. If the search base is defined more
specifically the engine can find the desired data quicker using less
resources.
In our environment the search base should be set to
“dc=med,dc=umich,dc=edu” (without the quotes).
Examples:
a.) Undesirable Search
base: ""
scope:2 dereference:0 sizelimit:1 timelimit:0 attrsonly:0
filter: "(mail=darthvader@med.umich.edu)"
Problem – No base defined
b) Preferred Search
base: "dc=med,dc=umich,dc=edu"
scope:2 dereference:0 sizelimit:1 timelimit:0 attrsonly:0
filter: "(uid=darthvader)"
Desired Attrs specified
2.) Dereference Aliases:
Dereference Aliases means to follow the alias pointer back to the data that
it points to. This is an expensive operation. In our LDAP data store we do
not use aliases, but we do use alias outside of the recommended search base.
If the search base is defined as specified above there will be no issues with
aliases. But to be careful any search should be configured to NOT dereference
aliases.
Examples
a) Undesirable
base: "dc=med,dc=umich,dc=edu"
scope:2 dereference:0 sizelimit:0 timelimit:0 attrsonly:0
filter: "(uid=darthvader)"
attribute: "surname"
b) Preferred
base: "dc=med,dc=umich,dc=edu"
scope:2 dereference:3 sizelimit:0 timelimit:0 attrsonly:0
filter: "(uid=darthvader)"
attribute: "surname"
attribute: "objectclass"
attribute: "subschemaSubentry"
3.) Search for Users by UID Attribute:
To locate users in LDAP, the uid attribute should be used. This value will be
the same as a uniquename.
Examples
a) Undesirable search
base: "dc=med,dc=umich,dc=edu"
scope:2 dereference:0 sizelimit:25 timelimit:10 attrsonly:0
filter: "(&(objectclass=person)(cn=darthvader,ou=people,dc=med,dc=umich,dc=edu)"
attribute: "cn"
Problem – CN search not uid search
b) Preferred search
Search request:
base: "dc=med,dc=umich,dc=edu"
scope:2 dereference:0 sizelimit:25 timelimit:10 attrsonly:0
filter: "(&(objectclass=person)(uid=darthvader))"
attribute: "cn"
4.) Specify Desired Attributes to be Returned:
Whenever possible the specific attributes desired should be requested.
Searches that do not have attributes defined will automatically retrieve all
object attributes. To optimize searches for performance specify desired
attributes.
Examples
a) Undesirable Search
Search request:
base: "cn=darthvader,ou=people,dc=med,dc=umich,dc=edu"
scope:0 dereference:3 sizelimit:0 timelimit:0 attrsonly:0
filter: "(objectClass=*)"
no attributes
Empty attribute list implies all user attributes
Problem – No attrs specified
b) Preferred Search
Search request:
base: "cn= darthvader,ou=people,dc=med,dc=umich,dc=edu"
scope:0 dereference:3 sizelimit:0 timelimit:0 attrsonly:0
filter: "(objectClass=*)"
attribute: "groupMembership"
attribute: "mail"
attribute: "uid"
Desired attrs specified
5.) Group Searches:
When searching groups for members, specify the specific groups necessary. If
not specified the member attribute of all groups will be searched each and
every time the search is invoked.
To identify the user being evaluated, do not use a hardcoded context, rather
specify the fdn returned as your member= value in you search string. This
will help prevent any problems or rework long term in the event the LDAP
structure is expanded, or changed.
Examples:
a) Undesirable Search:
Search request:
base: "dc=med,dc=umich,dc=edu"
scope:2 dereference:3 sizelimit:0 timelimit:0 attrsonly:0
filter:
"(&(objectClass=group)(member=cn=cpeterff,ou=people,dc=med,dc=umich,dc=edu))"
attribute: "cn"
Problem - No groups specified
b) Preferred Search
base: "dc=med,dc=umich,dc=edu"
scope:2 dereference:0 sizelimit:0 timelimit:0 attrsonly:0
filter: "(&(objectClass=Group)(|(cn=mcit-iso*)(cn=umhs*))(member=cn=darthvader,ou=people,dc=med,dc=umich,dc=edu))"
Specific groups are defined. Wildcards may be used.
Establishing a
Connection to the LDAP Service:
|
Parameter
|
Pre-Prod
|
Prod
|
|
DNS Name
|
ldap.p-ent.med.umich.edu
|
ldap.ent.med.umich.edu
|
|
Base DN:
|
dc = med, dc = umich, dc = edu
|
dc = med, dc = umich, dc = edu
|
|
Port
|
636
|
636
|
|
Principle
|
cn = {System Account}
Contact Account Admin to have account created and IDM to have
appropriate rights set-up.
|
cn = {System Account}
Contact Account Admin to have account created and IDM to have
appropriate rights set-up.
|
|
Mechanism
|
Simple
|
Simple
|
|
SSL
|
Yes
|
Yes
|
Error Handling:
A user may receive an error message when attempting to
authenticate to an LDAP directory. Below is a list of error message indexes
and the corresponding response that a user sees. Click here for the error messages file in XML format.
|
Message Index
|
Response Given to User
|
|
0x80070005
|
You have insufficient rights to
perform required operation
|
|
0x8007052E
|
User Name or Password you have
provided is incorrect
|
|
0x80072030
|
User Name you have provided is
incorrect
|
|
0x80072035
|
Your account is locked out or has
expired. Please contact MCIT Help Desk
|
|
-215
|
Please enter a unique password.
Password cannot be reused
|
|
-216
|
Password Reset Error: password must
be at least 6 characters long
|
|
-601
|
User Name you have provided is
incorrect
|
|
-669
|
Password you have provided is
incorrect.
|
|
-222
|
Password you have provided is bad.
|
|
-672
|
Update Error: insufficient rights
|
|
-197
|
Your account has been locked out for
a period of time. You have tried the incorrect password too many times
|
|
-220
|
Your account has expired. Please
contact MCIT Help Desk
|
Last updated: 05/25/2006
|